Scope
- *.Tapplock.com
- Tapplock Android and iPhone App
- Tapplock Enterprise Android App
- Tapplock Enterprise User Android App
- Tapplock one+
- Tapplock lite
Qualifying and Non Qualifying Submissions
Qualifying Vulnerabilities
- Any software / firmware design or implementation issue that substantially affects the confidentiality or integrity of user data is likely to be in scope for the program. Common examples include:
- Broken Authentication
- Authentication and Authorization Flaws
- Remote Code Execution
- Injection attacks
- Sensitive Information leaks or disclosure
- Hardware related issues
- Known vulnerabilities
- Bugs that require exceedingly UNLIKELY user interactions
- Out of date systems (mobile systems/older app)
- Disclosure of public information and information that does not present significant risk.
- Bugs that have already been submitted by another user, that we are already aware of, or that are classified as ineligible by Tapplock.
- Bugs that are in content/services not owned by Tapplock.
- Brute forcing of intended functionality.
- Reports recommending best practices without demonstrable proof of an actual issue.
- Speculative reports or reports without enough information to confirm an issue.
Rewards
Eligibility for any reward is made at Tapplock’s sole discretion under these general guidelines.
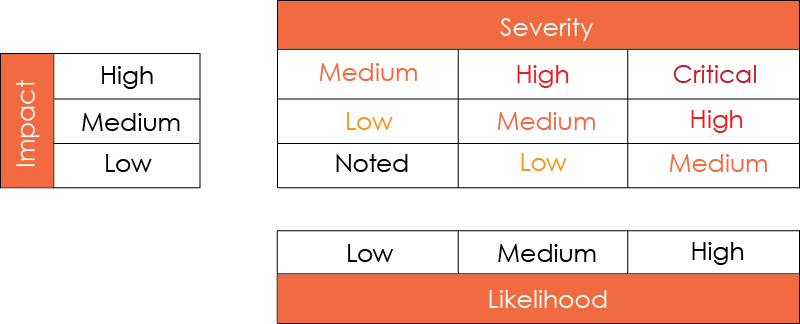
Low - $100-$300 USD
Medium - $300-$500 USD
High - $500-$1000 USD
Critical - $1000-$3000 USD
- Only one bounty will be awarded per vulnerability
- If we receive multiple reports for the same vulnerability, only the first person offering the first clear report will receive a reward
- Tapplock will award a bounty depending on the likelihood and impact of the vulnerability

Low - $100-$300 USD
Medium - $300-$500 USD
High - $500-$1000 USD
Critical - $1000-$3000 USD
Submission Process
Tapplock requires researchers to provide as much detail as possible when submitting a report. This will help us recreate and fix all valid reports as quickly as possible. Tapplock will exercise reasonable efforts to clarify indecipherable or incomplete submissions, but more complete submissions are often eligible for higher bounties. To help with this we require that all researchers download the submission form and fill it out fully. There are no restrictions on the number of qualified submissions an individual researcher can provide and potentially be paid bounties for.
Our Engineers will review the submission and verify its eligibility. The review time will vary depending on the complexity and completeness of your submission, as well as on the number of submissions we receive.
Once your submission has been reviewed and the Bug has been reproduced and fixed we will then consider whether your submission is eligible for a reward. If your submission is eligible for a reward we will then contact you to arrange payment. We will recognize all individuals who have been awarded through our Online Security Services Acknowledgments.
Please ensure the file you submit is encrypted with our PGP Key and that the subject line of your email is a brief description of the Bug. Unencrypted submissions will not be accepted. All submissions can be sent to bounty@tapplock.com
Submission form
PGP key
Our Engineers will review the submission and verify its eligibility. The review time will vary depending on the complexity and completeness of your submission, as well as on the number of submissions we receive.
Once your submission has been reviewed and the Bug has been reproduced and fixed we will then consider whether your submission is eligible for a reward. If your submission is eligible for a reward we will then contact you to arrange payment. We will recognize all individuals who have been awarded through our Online Security Services Acknowledgments.
Please ensure the file you submit is encrypted with our PGP Key and that the subject line of your email is a brief description of the Bug. Unencrypted submissions will not be accepted. All submissions can be sent to bounty@tapplock.com
Submission form
PGP key
FAQs
If I report a bug do I have to keep the bug confidential to receive a bounty?
If you file a report and publish the information publicly before we can fix it you will not receive any reward for the work you have done to locate the Bug. In the interest of protecting our users, we would appreciate a reasonable amount of time to address and issues that are reported to us.
Why don’t you provide a reward for denial-of-service bugs?
Denial-of-services bugs are generally less serious than other web application security bugs and in many cases don't require a technical vulnerability within the web application.
How long does it take to get the results of the review process after submitting a vulnerability report?
We try to start the review process as soon as the vulnerability is submitted, but please note that there is no set time frame for announcing results of the review process.
What do you mean by “duplicate’ submission and why was I not informed when I first submitted the report?
We consider any submission reporting a security vulnerability that was already know to us, either because of a previous bug bounty report or because we had already detected it ourselves, as a duplicate submission.
In order to best protect our customers, Tapplocks policy is to hold back on making any notifications on duplicate report conditions until we have remediated the potential exposure.
You fixed my bug, why have I not been paid?
We do not pay bounties on an individual basis at this time. All payments will be made on a quarterly basis.
Q1: January - March: Early May
Q2: April - June: Early August
Q3: July - September: Early November
Q4: October - December: Early February
If you file a report and publish the information publicly before we can fix it you will not receive any reward for the work you have done to locate the Bug. In the interest of protecting our users, we would appreciate a reasonable amount of time to address and issues that are reported to us.
Why don’t you provide a reward for denial-of-service bugs?
Denial-of-services bugs are generally less serious than other web application security bugs and in many cases don't require a technical vulnerability within the web application.
How long does it take to get the results of the review process after submitting a vulnerability report?
We try to start the review process as soon as the vulnerability is submitted, but please note that there is no set time frame for announcing results of the review process.
What do you mean by “duplicate’ submission and why was I not informed when I first submitted the report?
We consider any submission reporting a security vulnerability that was already know to us, either because of a previous bug bounty report or because we had already detected it ourselves, as a duplicate submission.
In order to best protect our customers, Tapplocks policy is to hold back on making any notifications on duplicate report conditions until we have remediated the potential exposure.
You fixed my bug, why have I not been paid?
We do not pay bounties on an individual basis at this time. All payments will be made on a quarterly basis.
Q1: January - March: Early May
Q2: April - June: Early August
Q3: July - September: Early November
Q4: October - December: Early February
Terms and Conditions
This web page represents a legal document with terms and conditions applicable to all individuals (“Researcher”) who have submitted a vulnerability with Tapplock Corp. (“Tapplock”).
Submission Process refers to the steps a Research must follow in order to submit a submission which are listed above.
Tapplock is unable to issue rewards to Researchers who are on sanctions lists, or who are in countries on sanctions lists.
Researchers are responsible for any tax implications depending on the country of residency and citizenship.
There may be additional restrictions on a Researcher’s ability to enter depending upon the Researcher’s local law.
This is an experimental and discretionary rewards program. Researchers should understand that Tapplock can cancel the program at any time and the decision as to whether or not to pay a reward has to be entirely at Tapplock’s discretion.
Testing must not violate any law or disrupt or compromise any data that is not the Researcher’s own.
Standard Program Rules
The Researcher hereby represent that the Researcher have obtained the necessary approvals and consents from all third parties including the Researcher’s employer for the purpose of participating as a Researcher.
For the purposes of this section, “Testing Results” means information about vulnerabilities discovered on Tapplock’s systems, found, observed or identified by Researchers.
The Researcher hereby agree and warrant that the Researcher will disclose all of the Testing Results found or identified by the Researcher (“Researcher’s Testing Results”) to Tapplock. Furthermore, the Researcher hereby assign to Tapplock and agree to assign to Tapplock any and all of the Researcher’s Testing Results and rights thereto. To the extent any rights in the Researcher’s Testing Results are not assignable, the Researcher shall grant and agree to grant to Tapplock under any and all such rights an irrevocable, paid-up, royalty free, perpetual, exclusive, sublicensable (directly or indirectly through multiple tiers), transferable, and worldwide license to use and permit others to use such Testing Results in any manner desired by Tapplock (and/or Tapplock’s customers and sponsors) without restriction or accounting to the Researcher, including, without limitation, the right to make, have made, sell, offer for sale, use, rent, lease, import, copy, prepare derivative works, publicly display, publicly perform, and distribute all or any part of such Testing Results and modifications and combinations thereof and to sublicense (directly or indirectly through multiple tiers) or transfer any and all such rights. Further, the Researcher shall waive and agree to waive in favor of Tapplock any moral right or other right or claim that is contrary to the intent of a complete transfer of rights to Tapplock in the Researcher’s Testing Results.
Confidentiality Obligations
“Confidential Information” means any information that is marked or otherwise designated as confidential at the time of disclosure or that a reasonable person would consider confidential based on the circumstances and content of the disclosure, and which is disclosed in connection with Tapplock’s Bounty Program. Confidential Information does not include information that: (i) is or becomes known to the receiving party from a source other than one having an obligation of confidentiality to the disclosing party; (ii) is or becomes publicly known or otherwise ceases to be confidential, except through a breach of this Agreement; or (iii) is independently developed by the receiving party.
Before engaging in any testing or submitting findings the Researcher agree that the Researcher will (i) hold in confidence and not disclose to any third party any Confidential Information, except as approved in writing by disclosing party; (ii) protect such Confidential Information with at least the same degree of care that the Researcher uses to protect its own Confidential Information, but in no case, less than reasonable care; (iii) use the disclosing party’s Confidential Information for no purpose other than the use permitted by the disclosing party; and (iv) immediately notify disclosing party upon discovery of any loss or unauthorized disclosure of disclosing party’s Confidential Information.
ALL SUBMISSIONS ARE CONFIDENTIAL INFORMATION OF TAPPLOCK UNLESS OTHERWISE STATED. This means no submissions may be publicly disclosed at any time unless Tapplock has otherwise consented to disclosure.
Support center
Submission Process refers to the steps a Research must follow in order to submit a submission which are listed above.
Tapplock is unable to issue rewards to Researchers who are on sanctions lists, or who are in countries on sanctions lists.
Researchers are responsible for any tax implications depending on the country of residency and citizenship.
There may be additional restrictions on a Researcher’s ability to enter depending upon the Researcher’s local law.
This is an experimental and discretionary rewards program. Researchers should understand that Tapplock can cancel the program at any time and the decision as to whether or not to pay a reward has to be entirely at Tapplock’s discretion.
Testing must not violate any law or disrupt or compromise any data that is not the Researcher’s own.
Standard Program Rules
- Submissions must follow our Submission Process to be considered for a reward.
- Actions which affect the integrity or availability of Tapplock’s programs are prohibited and strictly enforced. If a Researcher notices performance degradation on Tapplock’s systems, the Researcher must immediately suspend all use of automated tools.
- Submissions should have impact to the Scope’s security posture. Impact means the reported issue affects the Scope’s users, systems, or data security in a meaningful way. Researchers may be asked to defend the impact in order to qualify for a reward.
- Submissions may be closed if a Researcher is non-responsive to requests for information after 7 days.
- Tapplock’s Standard Program Rules apply to all submissions made through email to Tapplock, including Duplicates, Out of Scope, and Not Applicable submissions.
- A Researcher must be at least 18 years old or have reached the age of majority in the Researchers jurisdiction of primary residence and citizenship to be eligible to receive any monetary compensation.
The Researcher hereby represent that the Researcher have obtained the necessary approvals and consents from all third parties including the Researcher’s employer for the purpose of participating as a Researcher.
For the purposes of this section, “Testing Results” means information about vulnerabilities discovered on Tapplock’s systems, found, observed or identified by Researchers.
The Researcher hereby agree and warrant that the Researcher will disclose all of the Testing Results found or identified by the Researcher (“Researcher’s Testing Results”) to Tapplock. Furthermore, the Researcher hereby assign to Tapplock and agree to assign to Tapplock any and all of the Researcher’s Testing Results and rights thereto. To the extent any rights in the Researcher’s Testing Results are not assignable, the Researcher shall grant and agree to grant to Tapplock under any and all such rights an irrevocable, paid-up, royalty free, perpetual, exclusive, sublicensable (directly or indirectly through multiple tiers), transferable, and worldwide license to use and permit others to use such Testing Results in any manner desired by Tapplock (and/or Tapplock’s customers and sponsors) without restriction or accounting to the Researcher, including, without limitation, the right to make, have made, sell, offer for sale, use, rent, lease, import, copy, prepare derivative works, publicly display, publicly perform, and distribute all or any part of such Testing Results and modifications and combinations thereof and to sublicense (directly or indirectly through multiple tiers) or transfer any and all such rights. Further, the Researcher shall waive and agree to waive in favor of Tapplock any moral right or other right or claim that is contrary to the intent of a complete transfer of rights to Tapplock in the Researcher’s Testing Results.
Confidentiality Obligations
“Confidential Information” means any information that is marked or otherwise designated as confidential at the time of disclosure or that a reasonable person would consider confidential based on the circumstances and content of the disclosure, and which is disclosed in connection with Tapplock’s Bounty Program. Confidential Information does not include information that: (i) is or becomes known to the receiving party from a source other than one having an obligation of confidentiality to the disclosing party; (ii) is or becomes publicly known or otherwise ceases to be confidential, except through a breach of this Agreement; or (iii) is independently developed by the receiving party.
Before engaging in any testing or submitting findings the Researcher agree that the Researcher will (i) hold in confidence and not disclose to any third party any Confidential Information, except as approved in writing by disclosing party; (ii) protect such Confidential Information with at least the same degree of care that the Researcher uses to protect its own Confidential Information, but in no case, less than reasonable care; (iii) use the disclosing party’s Confidential Information for no purpose other than the use permitted by the disclosing party; and (iv) immediately notify disclosing party upon discovery of any loss or unauthorized disclosure of disclosing party’s Confidential Information.
ALL SUBMISSIONS ARE CONFIDENTIAL INFORMATION OF TAPPLOCK UNLESS OTHERWISE STATED. This means no submissions may be publicly disclosed at any time unless Tapplock has otherwise consented to disclosure.